


cyber security
Trending Blogposts on cyber security

The difference between Cyber-Security and Ethical-Hacking
In this blog, we will discuss the difference between Cyber-Security and Ethical-Hacking.
Read in 6 minutesEthical-Hacking
Overview of Cyber Security
In this blog, we will discuss Cyber Security.
Read in 7 minutesCyber-Security
Advanced Persistent Threats
In this blog post, we will discuss Advanced Persistent Threats.
Read in 16 minutesEthical-Hacking
Cyber Security Challenges in 2022
In this blog, we will discuss Cyber Security Challenges in 2022.
Read in 12 minutesCyber-Security
Cyber Marketing
In this blog, we will discuss Cyber Marketing.
Read in 11 minutesCyber-Security
White Hat Hackers : Overview
In this article, we will know about the White Hat Hackers overview.
Read in 9 minutesEthical-Hacking
Capture the Flag (CTF)-Top 10 Cyber Hacking Competitions
Here in this article, we’ll let you know about the 10 best Capture the Flag cyber hacking competitions.
Read in 10 minutesCTF
Cyber Crime in India
Today in this blog, we will discuss Cyber Crime in India.
Read in 11 minutesCyber-Security
Ethical Hacker Definition .
In this article, we will know about the Ethical Hacker Definition.
Read in 16 minutesEthical-Hacking
Process of Hacking
In this article, we will know about the Process of Hacking.
Read in 8 minutesEthical-Hacking
Types of Cyber Security
In this blog, we will discuss types of Cyber Security.
Read in 12 minutesCyber-Security
Hardware Hacking
In this article, we will know about the Hardware Hacking.
Read in 10 minutesEthical-Hacking
Cyber Forensics
In this blog, we will discuss Cyber Forensics
Read in 9 minutesCyber-Security
Malware Analysis
In this blog, we will discuss Malware Analysis.
Read in 10 minutesCyber-Security
CCNA Commands
In this blog post, We will discuss the CCNA Commands.
Read in 11 minutesEthical-Hacking
Cyber Law
In this blog, we will discuss Cyber Law.
Read in 8 minutesCyber-Security
Types of Computer Worms
In this blog, we will discuss Types of Computer Worms.
Read in 11 minutesCyber-Security
Pretty Good Privacy
In this blog, we will discuss Pretty Good Privacy.
Read in 9 minutesCyber-Security
Data Breach
In this blog, we will discuss Data Breach.
Read in 7 minutesCyber-Security
Incognito Mode
In this blog, we will discuss Incognito Mode.
Read in 8 minutesCyber-Security
Nmap: an overview.
In this blog, we will discuss Nmap an overview.
Read in 6 minutesEthical-Hacking
Nmap Commands
We will know in this article, what's Nmap Commands.
Read in 10 minutesEthical-Hacking
Malware : an Overview.
We will know in this article, what's Malware an Overview.
Read in 6 minutesEthical-Hacking
Types of Malware
We will know in this article, what're the Types of Malware.
Read in 14 minutesEthical-Hacking
Malware Removal Tools
In this blog, we will discuss Malware Removal Tools.
Read in 10 minutesEthical-Hacking
IDS: An Overview
We will know in this article, what're IDS and its Overview.
Read in 7 minutesEthical-Hacking
IDS Tools
We will know in this article, what's IDS Tools.
Read in 10 minutesEthical-Hacking
Threat Hunting : An overview
In this blog post, We will discuss Threat Hunting An overview.
Read in 10 minutesEthical-Hacking
Threat Hunting Tools
We will know in this article, what's the Threat Hunting Tools.
Read in 10 minutesEthical-Hacking
Threat Intelligence Feeds
In this blog, We will discuss Threat Intelligence Feeds.
Read in 11 minutesEthical-Hacking
Threat to E Commerce
In this blog, we will discuss Threat to E Commerce.
Read in 9 minutesEthical-Hacking
Data Recovery techniques
We will know in this article, what's Data Recovery techniques.
Read in 22 minutesEthical-Hacking
LDAP Injection
We will know in this article, what's LDAP Injection.
Read in 11 minutesEthical-Hacking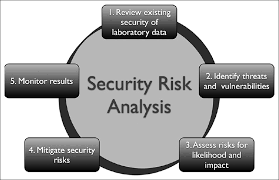
Security Risk Analysis
In this blog, We will discuss Security Risk Analysis.
Read in 11 minutesEthical-Hacking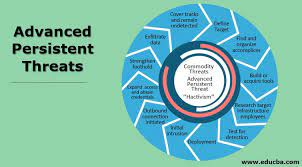
Advanced Persistent Threats
In this blog, We will discuss Advanced Persistent Threats.
Read in 14 minutesEthical-Hacking
Nmap usage
We will know in this article, what's Nmap usage.
Read in 8 minutesEthical-Hacking
Cheat Sheet CCNA
We will know in this article, what's the Cheat Sheet CCNA.
Read in 7 minutesEthical-Hacking
Is Ansible free
We will know in this article, what're the Is Ansible free.
Read in 9 minutesEthical-Hacking
Why is a proxy server important for cyber security?
Statistics point to a growing number of cybercrime cases across the world, which has led to unprecedented losses for both businesses and individuals.
Read in 10 minutesCyber-Security
Build your successful career in cyber security
Salary · 1. Entry-level. Cybersecurity specialist/ Technician – $75,000; Cybercrime Analyst/ Investigator – $85,000; Incident Analyst/ Responder – $99,000; IT.
Read in 11 minutesCyber-Security
How to install and configure Nessus with nginx in Ubuntu?
Like most scanners, Nessus is used during penetration testing and vulnerability assessments, including malicious assaults. It is a program that scans computers for security holes.
Read in 4 minutesPenetration Testing
The Best way to install Hydra on Ubuntu Docker!
Hydra is a brute-forcing tool that helps penetration testers and ethical hackers crack the passwords of network services.
Read in 2 minutesCyber-Security
How to install Metaslpoit on Ubuntu?
The Metasploit Framework is an open source platform that supports vulnerability research, exploit development, and the creation of custom security tools.
Read in 2 minutesCyber-Security
What distinguishes Kali Linux from Ubuntu? The benefits and drawbacks of each operating system (OS)!
Ubuntu is primarily an operating system much like Windows for computers, while Kali Linux is all about security improvement.
Read in 5 minutesLinux Administration
Understand the fundamental types of protocols and their corresponding port numbers for use in networking.
A network protocol is an established set of rules that determine how data is transmitted between different devices in the same network
Read in 6 minutesNetworking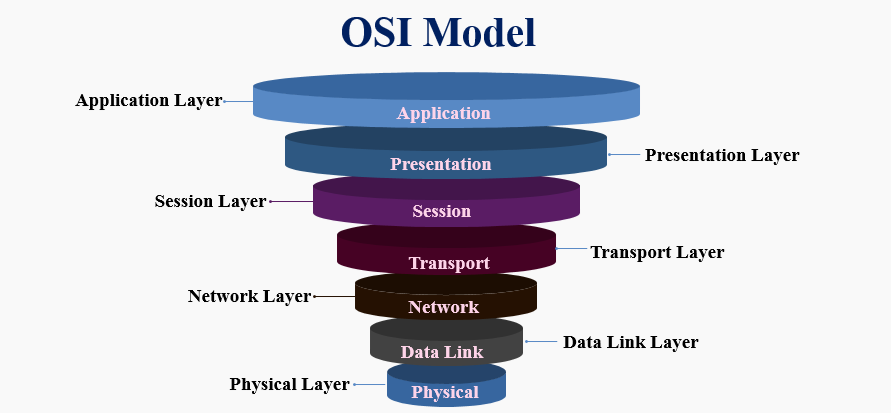
Here is the complete OSI module description from the networkin blog.
The Open Systems Interconnection (OSI) model describes seven layers that computer systems use to communicate over a network.
Read in 8 minutesNetworkingPopular Discussions on cyber security
cyber security
Trending Blogposts on cyber security

The difference between Cyber-Security and Ethical-Hacking
In this blog, we will discuss the difference between Cyber-Security and Ethical-Hacking.
Read in 6 minutesEthical-Hacking
Overview of Cyber Security
In this blog, we will discuss Cyber Security.
Read in 7 minutesCyber-Security
Advanced Persistent Threats
In this blog post, we will discuss Advanced Persistent Threats.
Read in 16 minutesEthical-Hacking
Cyber Security Challenges in 2022
In this blog, we will discuss Cyber Security Challenges in 2022.
Read in 12 minutesCyber-Security
Cyber Marketing
In this blog, we will discuss Cyber Marketing.
Read in 11 minutesCyber-Security
White Hat Hackers : Overview
In this article, we will know about the White Hat Hackers overview.
Read in 9 minutesEthical-Hacking
Capture the Flag (CTF)-Top 10 Cyber Hacking Competitions
Here in this article, we’ll let you know about the 10 best Capture the Flag cyber hacking competitions.
Read in 10 minutesCTF
Cyber Crime in India
Today in this blog, we will discuss Cyber Crime in India.
Read in 11 minutesCyber-Security
Ethical Hacker Definition .
In this article, we will know about the Ethical Hacker Definition.
Read in 16 minutesEthical-Hacking
Process of Hacking
In this article, we will know about the Process of Hacking.
Read in 8 minutesEthical-Hacking
Types of Cyber Security
In this blog, we will discuss types of Cyber Security.
Read in 12 minutesCyber-Security
Hardware Hacking
In this article, we will know about the Hardware Hacking.
Read in 10 minutesEthical-Hacking
Cyber Forensics
In this blog, we will discuss Cyber Forensics
Read in 9 minutesCyber-Security
Malware Analysis
In this blog, we will discuss Malware Analysis.
Read in 10 minutesCyber-Security
CCNA Commands
In this blog post, We will discuss the CCNA Commands.
Read in 11 minutesEthical-Hacking
Cyber Law
In this blog, we will discuss Cyber Law.
Read in 8 minutesCyber-Security
Types of Computer Worms
In this blog, we will discuss Types of Computer Worms.
Read in 11 minutesCyber-Security
Pretty Good Privacy
In this blog, we will discuss Pretty Good Privacy.
Read in 9 minutesCyber-Security
Data Breach
In this blog, we will discuss Data Breach.
Read in 7 minutesCyber-Security
Incognito Mode
In this blog, we will discuss Incognito Mode.
Read in 8 minutesCyber-Security
Nmap: an overview.
In this blog, we will discuss Nmap an overview.
Read in 6 minutesEthical-Hacking
Nmap Commands
We will know in this article, what's Nmap Commands.
Read in 10 minutesEthical-Hacking
Malware : an Overview.
We will know in this article, what's Malware an Overview.
Read in 6 minutesEthical-Hacking
Types of Malware
We will know in this article, what're the Types of Malware.
Read in 14 minutesEthical-Hacking
Malware Removal Tools
In this blog, we will discuss Malware Removal Tools.
Read in 10 minutesEthical-Hacking
IDS: An Overview
We will know in this article, what're IDS and its Overview.
Read in 7 minutesEthical-Hacking
IDS Tools
We will know in this article, what's IDS Tools.
Read in 10 minutesEthical-Hacking
Threat Hunting : An overview
In this blog post, We will discuss Threat Hunting An overview.
Read in 10 minutesEthical-Hacking
Threat Hunting Tools
We will know in this article, what's the Threat Hunting Tools.
Read in 10 minutesEthical-Hacking
Threat Intelligence Feeds
In this blog, We will discuss Threat Intelligence Feeds.
Read in 11 minutesEthical-Hacking
Threat to E Commerce
In this blog, we will discuss Threat to E Commerce.
Read in 9 minutesEthical-Hacking
Data Recovery techniques
We will know in this article, what's Data Recovery techniques.
Read in 22 minutesEthical-Hacking
LDAP Injection
We will know in this article, what's LDAP Injection.
Read in 11 minutesEthical-Hacking
Security Risk Analysis
In this blog, We will discuss Security Risk Analysis.
Read in 11 minutesEthical-Hacking
Advanced Persistent Threats
In this blog, We will discuss Advanced Persistent Threats.
Read in 14 minutesEthical-Hacking
Nmap usage
We will know in this article, what's Nmap usage.
Read in 8 minutesEthical-Hacking
Cheat Sheet CCNA
We will know in this article, what's the Cheat Sheet CCNA.
Read in 7 minutesEthical-Hacking
Is Ansible free
We will know in this article, what're the Is Ansible free.
Read in 9 minutesEthical-Hacking
Why is a proxy server important for cyber security?
Statistics point to a growing number of cybercrime cases across the world, which has led to unprecedented losses for both businesses and individuals.
Read in 10 minutesCyber-Security
Build your successful career in cyber security
Salary · 1. Entry-level. Cybersecurity specialist/ Technician – $75,000; Cybercrime Analyst/ Investigator – $85,000; Incident Analyst/ Responder – $99,000; IT.
Read in 11 minutesCyber-Security
How to install and configure Nessus with nginx in Ubuntu?
Like most scanners, Nessus is used during penetration testing and vulnerability assessments, including malicious assaults. It is a program that scans computers for security holes.
Read in 4 minutesPenetration Testing
The Best way to install Hydra on Ubuntu Docker!
Hydra is a brute-forcing tool that helps penetration testers and ethical hackers crack the passwords of network services.
Read in 2 minutesCyber-Security
How to install Metaslpoit on Ubuntu?
The Metasploit Framework is an open source platform that supports vulnerability research, exploit development, and the creation of custom security tools.
Read in 2 minutesCyber-Security
What distinguishes Kali Linux from Ubuntu? The benefits and drawbacks of each operating system (OS)!
Ubuntu is primarily an operating system much like Windows for computers, while Kali Linux is all about security improvement.
Read in 5 minutesLinux Administration
Understand the fundamental types of protocols and their corresponding port numbers for use in networking.
A network protocol is an established set of rules that determine how data is transmitted between different devices in the same network
Read in 6 minutesNetworking
Here is the complete OSI module description from the networkin blog.
The Open Systems Interconnection (OSI) model describes seven layers that computer systems use to communicate over a network.
Read in 8 minutesNetworking