


networking
Trending Blogposts on networking

Using Terraform to Create a New VPC and Public Subnet in GCP
Creating a virtual private network and subnetworks is the foundation of using resources or any infrastructure within GCP
Read in 3 minutesTerraform
Amazon ECS vs EKS: Which Service is Right for You
In this blog we will discuss which is best Amazon Web Service in ECS vs EKS.
Read in 5 minutesAmazon Web Service (AWS)
Python - Network Programming
Today we will cover Python - Network Programming.
Read in 11 minutesPython
10 WEB SECURITY TOOLS TO IDENTIFY VULNERABILITIES
Today we will discuss 10 WEB SECURITY TOOLS TO IDENTIFY VULNERABILITIES.
Read in 16 minutesWeb Security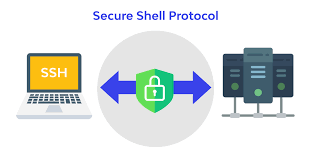
How can SSH be installed in Ubuntu?
SSH is a software package that enables secure system administration and file transfers over insecure networks.
Read in 2 minutesServer Administration
Understand the fundamental types of protocols and their corresponding port numbers for use in networking.
A network protocol is an established set of rules that determine how data is transmitted between different devices in the same network
Read in 6 minutesNetworking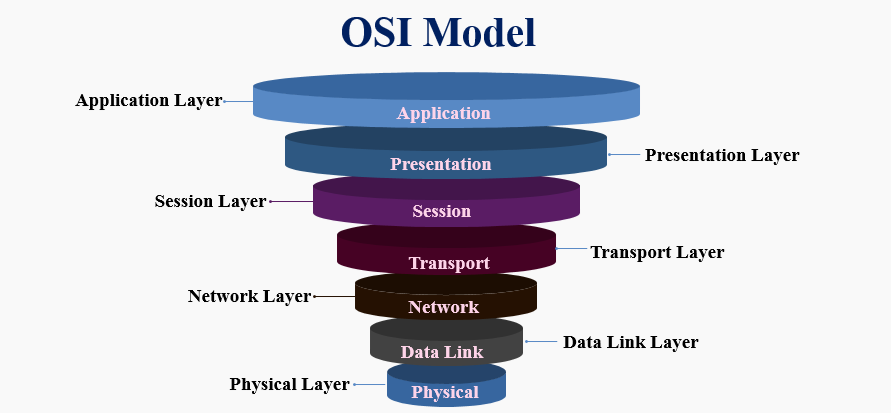
Here is the complete OSI module description from the networkin blog.
The Open Systems Interconnection (OSI) model describes seven layers that computer systems use to communicate over a network.
Read in 8 minutesNetworkingPopular Discussions on networking
openWhat is the difference between a port and a socket?
1
0
0
openabout IP packet through router
1
0
0
openHow a Switch creates a separate Collision Network on each port?
1
0
0
openWhat is the application layer specifically?
1
0
0
openHow is Docker different from a virtual machine?
1
0
0
openHow can you find out which process is listening on a TCP or UDP port on Windows?
0
0
0
openGenerating random whole numbers in JavaScript in a specific range?
2
1
0
openIs it possible to disable the network in iOS Simulator?
0
0
0
openDisabling Chrome cache for website development
1
0
0
openWhat is the difference between a URI, a URL and a URN?
1
0
0
openHow to remove old Docker containers
1
0
0
openBlackberry firewall "connection inside and outside the firewall" problem
0
0
0
openWhat can GNS3 and Packet Tracer be used for besides simulations?
0
0
0
openhow to extract video file from pcap file using python
5
0
0
openRecording current size of the queue of OpenFlow Switches on passing traffic in Mininet
1
0
0
openHow to access AWS SNS from an application served by internal classic load balancer?
2
0
0
openWhat is the function of 802.11 (Retry Field)?
2
0
0
openActive Directory GPO
2
0
0
openHow do I set up my Linux VM to act in the same network as my windows host system
1
0
0
openGetting key from different server
3
0
1
openWhile subnetting Class B address how to find out subnets number?
3
1
0
networking
Trending Blogposts on networking

Using Terraform to Create a New VPC and Public Subnet in GCP
Creating a virtual private network and subnetworks is the foundation of using resources or any infrastructure within GCP
Read in 3 minutesTerraform
Amazon ECS vs EKS: Which Service is Right for You
In this blog we will discuss which is best Amazon Web Service in ECS vs EKS.
Read in 5 minutesAmazon Web Service (AWS)
Python - Network Programming
Today we will cover Python - Network Programming.
Read in 11 minutesPython
10 WEB SECURITY TOOLS TO IDENTIFY VULNERABILITIES
Today we will discuss 10 WEB SECURITY TOOLS TO IDENTIFY VULNERABILITIES.
Read in 16 minutesWeb Security
How can SSH be installed in Ubuntu?
SSH is a software package that enables secure system administration and file transfers over insecure networks.
Read in 2 minutesServer Administration
Understand the fundamental types of protocols and their corresponding port numbers for use in networking.
A network protocol is an established set of rules that determine how data is transmitted between different devices in the same network
Read in 6 minutesNetworking
Here is the complete OSI module description from the networkin blog.
The Open Systems Interconnection (OSI) model describes seven layers that computer systems use to communicate over a network.
Read in 8 minutesNetworking