


Ethical-Hacking
Ethical Hacking is an authorized practice of bypassing system security to identify potential data breaches and threats in a network. The company that owns the system or network allows Cyber Security engineers to perform such activities in order to test the system’s defenses. Thus, unlike malicious hacking, this process is planned, approved, and more importantly, legal.
Trending Blogposts on Ethical-Hacking

How to use GoldenEye's DDos attack method to exploit or take down a server or web application?
DDoS (Distributed Denial of Service) is a category of malicious cyber-attacks that hackers or cybercriminals employ in order to make an machine unavailable to its intended users on the Internet.
Read in 4 minutesEthical-Hacking
How can I use the Bettercap Tool to hack into a target's account or steal their data?
BetterCAP is a powerful, flexible and portable tool created to perform various types of MITM attacks against a network, manipulate HTTP, HTTPS and TCP traffic in realtime, sniff for credentials.
Read in 3 minutesEthical-Hacking
What distinguishes Kali Linux from Parrot OS? The benefits and drawbacks of each operating system (OS)!
Parrot OS and Kali Linux are similar to each other , and is an open-source Debian-based operating system and both are used for Penetration Testing.
Read in 4 minutesEthical-Hacking
Is Ansible free
We will know in this article, what're the Is Ansible free.
Read in 9 minutesEthical-Hacking
Cheat Sheet CCNA
We will know in this article, what's the Cheat Sheet CCNA.
Read in 7 minutesEthical-Hacking
Nmap Scan Types
We will know in this article, what's Nmap Scan Types.
Read in 11 minutesEthical-Hacking
Nmap usage
We will know in this article, what's Nmap usage.
Read in 8 minutesEthical-Hacking
Advanced Persistent Threats
In this blog, We will discuss Advanced Persistent Threats.
Read in 14 minutesEthical-Hacking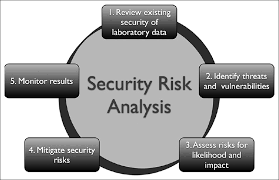
Security Risk Analysis
In this blog, We will discuss Security Risk Analysis.
Read in 11 minutesEthical-Hacking
LDAP Injection
We will know in this article, what's LDAP Injection.
Read in 11 minutesEthical-Hacking
Process of Reverse Engineering
We will know in this article, what's Process of Reverse Engineering is.
Read in 10 minutesEthical-Hacking
Data Recovery techniques
We will know in this article, what's Data Recovery techniques.
Read in 22 minutesEthical-Hacking
Threat to E Commerce
In this blog, we will discuss Threat to E Commerce.
Read in 9 minutesEthical-Hacking
Threat Intelligence Feeds
In this blog, We will discuss Threat Intelligence Feeds.
Read in 11 minutesEthical-Hacking
Threat Hunting Tools
We will know in this article, what's the Threat Hunting Tools.
Read in 10 minutesEthical-Hacking
Threat Hunting : An overview
In this blog post, We will discuss Threat Hunting An overview.
Read in 10 minutesEthical-Hacking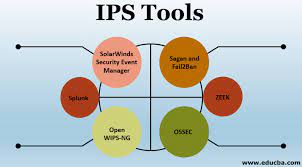
IDS Tools
We will know in this article, what's IDS Tools.
Read in 10 minutesEthical-Hacking
IDS: An Overview
We will know in this article, what're IDS and its Overview.
Read in 7 minutesEthical-Hacking
Malware Removal Tools
In this blog, we will discuss Malware Removal Tools.
Read in 10 minutesEthical-Hacking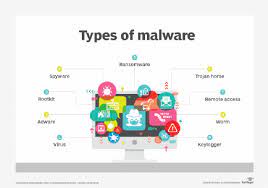
Types of Malware
We will know in this article, what're the Types of Malware.
Read in 14 minutesEthical-Hacking
Malware : an Overview.
We will know in this article, what's Malware an Overview.
Read in 6 minutesEthical-Hacking
Nmap Commands
We will know in this article, what's Nmap Commands.
Read in 10 minutesEthical-Hacking
Nmap: an overview.
In this blog, we will discuss Nmap an overview.
Read in 6 minutesEthical-Hacking
CCNA Commands
In this blog post, We will discuss the CCNA Commands.
Read in 11 minutesEthical-Hacking
Hardware Hacking
In this article, we will know about the Hardware Hacking.
Read in 10 minutesEthical-Hacking
Process of Hacking
In this article, we will know about the Process of Hacking.
Read in 8 minutesEthical-Hacking
Ethical Hacker Definition .
In this article, we will know about the Ethical Hacker Definition.
Read in 16 minutesEthical-Hacking
Ethical Hacking Tools: Overview
In this article, we will know about the Ethical Hacking Tools overview.
Read in 12 minutesEthical-Hacking
White Hat Hackers : Overview
In this article, we will know about the White Hat Hackers overview.
Read in 9 minutesEthical-Hacking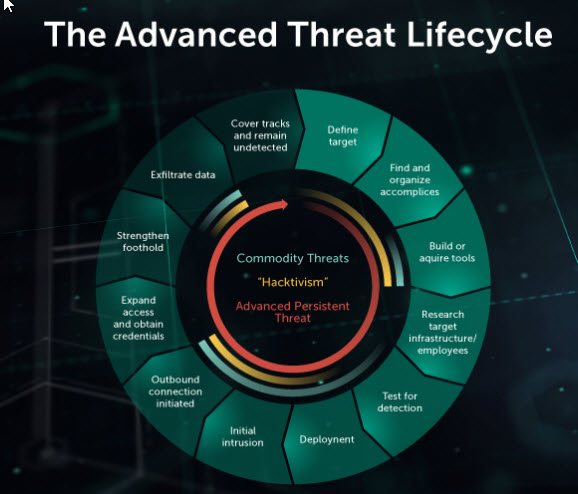
Advanced Persistent Threats
In this blog post, we will discuss Advanced Persistent Threats.
Read in 16 minutesEthical-Hacking
Overview: Black Hat Hackers
In this article, we will know about the Black Hat Hackers overview.
Read in 6 minutesEthical-Hacking
Process of Hacking
In this blog, we will discuss the Process of Hacking.
Read in 8 minutesEthical-Hacking
The difference between Cyber-Security and Ethical-Hacking
In this blog, we will discuss the difference between Cyber-Security and Ethical-Hacking.
Read in 6 minutesEthical-Hacking
Overview of Ethical Hacking
Today, we will discuss Ethical Hacking.
Read in 7 minutesEthical-Hacking
How to write a Script to Perform a Vulnerability Scan of the Listed Services
Let's quickly write an automated vulnerability scan of the server using Python. This Python script will make use of Nmap
Read in 3 minutesEthical-Hacking
Blogpost
1120 posts
Discussion Threads
1572 discussions
Interview Questions
9183 questions
Cheatsheets
coming soonTechnologies
107 categories
Questionaire
coming soonPopular Discussions on Ethical-Hacking
openwhy is my camphish hacking tool pictures not loading in?
1
0
0
openHave you ever done SQL injection?
1
0
0
openPHP and Ethical Hacking
1
0
0
openpynput not importing even though it is installed
1
0
0
openHave you ever done SQL injection?
1
0
0
openis linux based system needed for python hacking?
3
1
0
openWhen learning ethical web hacking, should I learn javascript, html, or both
3
1
0
openPHP and Ethical Hacking
1
0
0
openSQL Injection ethical hacking
1
0
0
openThe definitive guide to form-based website authentication
2
0
0
openEthical Hack Changing Request Headers to Access Restricted Page ASP.NET
0
0
0
openEthical hacking script not working - no error message
1
0
0
Ethical-Hacking
Ethical Hacking is an authorized practice of bypassing system security to identify potential data breaches and threats in a network. The company that owns the system or network allows Cyber Security engineers to perform such activities in order to test the system’s defenses. Thus, unlike malicious hacking, this process is planned, approved, and more importantly, legal.
Trending Blogposts on Ethical-Hacking

How to use GoldenEye's DDos attack method to exploit or take down a server or web application?
DDoS (Distributed Denial of Service) is a category of malicious cyber-attacks that hackers or cybercriminals employ in order to make an machine unavailable to its intended users on the Internet.
Read in 4 minutesEthical-Hacking
How can I use the Bettercap Tool to hack into a target's account or steal their data?
BetterCAP is a powerful, flexible and portable tool created to perform various types of MITM attacks against a network, manipulate HTTP, HTTPS and TCP traffic in realtime, sniff for credentials.
Read in 3 minutesEthical-Hacking
What distinguishes Kali Linux from Parrot OS? The benefits and drawbacks of each operating system (OS)!
Parrot OS and Kali Linux are similar to each other , and is an open-source Debian-based operating system and both are used for Penetration Testing.
Read in 4 minutesEthical-Hacking
Is Ansible free
We will know in this article, what're the Is Ansible free.
Read in 9 minutesEthical-Hacking
Cheat Sheet CCNA
We will know in this article, what's the Cheat Sheet CCNA.
Read in 7 minutesEthical-Hacking
Nmap Scan Types
We will know in this article, what's Nmap Scan Types.
Read in 11 minutesEthical-Hacking
Nmap usage
We will know in this article, what's Nmap usage.
Read in 8 minutesEthical-Hacking
Advanced Persistent Threats
In this blog, We will discuss Advanced Persistent Threats.
Read in 14 minutesEthical-Hacking
Security Risk Analysis
In this blog, We will discuss Security Risk Analysis.
Read in 11 minutesEthical-Hacking
LDAP Injection
We will know in this article, what's LDAP Injection.
Read in 11 minutesEthical-Hacking
Process of Reverse Engineering
We will know in this article, what's Process of Reverse Engineering is.
Read in 10 minutesEthical-Hacking
Data Recovery techniques
We will know in this article, what's Data Recovery techniques.
Read in 22 minutesEthical-Hacking
Threat to E Commerce
In this blog, we will discuss Threat to E Commerce.
Read in 9 minutesEthical-Hacking
Threat Intelligence Feeds
In this blog, We will discuss Threat Intelligence Feeds.
Read in 11 minutesEthical-Hacking
Threat Hunting Tools
We will know in this article, what's the Threat Hunting Tools.
Read in 10 minutesEthical-Hacking
Threat Hunting : An overview
In this blog post, We will discuss Threat Hunting An overview.
Read in 10 minutesEthical-Hacking
IDS Tools
We will know in this article, what's IDS Tools.
Read in 10 minutesEthical-Hacking
IDS: An Overview
We will know in this article, what're IDS and its Overview.
Read in 7 minutesEthical-Hacking
Malware Removal Tools
In this blog, we will discuss Malware Removal Tools.
Read in 10 minutesEthical-Hacking
Types of Malware
We will know in this article, what're the Types of Malware.
Read in 14 minutesEthical-Hacking
Malware : an Overview.
We will know in this article, what's Malware an Overview.
Read in 6 minutesEthical-Hacking
Nmap Commands
We will know in this article, what's Nmap Commands.
Read in 10 minutesEthical-Hacking
Nmap: an overview.
In this blog, we will discuss Nmap an overview.
Read in 6 minutesEthical-Hacking
CCNA Commands
In this blog post, We will discuss the CCNA Commands.
Read in 11 minutesEthical-Hacking
Hardware Hacking
In this article, we will know about the Hardware Hacking.
Read in 10 minutesEthical-Hacking
Process of Hacking
In this article, we will know about the Process of Hacking.
Read in 8 minutesEthical-Hacking
Ethical Hacker Definition .
In this article, we will know about the Ethical Hacker Definition.
Read in 16 minutesEthical-Hacking
Ethical Hacking Tools: Overview
In this article, we will know about the Ethical Hacking Tools overview.
Read in 12 minutesEthical-Hacking
White Hat Hackers : Overview
In this article, we will know about the White Hat Hackers overview.
Read in 9 minutesEthical-Hacking
Advanced Persistent Threats
In this blog post, we will discuss Advanced Persistent Threats.
Read in 16 minutesEthical-Hacking
Overview: Black Hat Hackers
In this article, we will know about the Black Hat Hackers overview.
Read in 6 minutesEthical-Hacking
Process of Hacking
In this blog, we will discuss the Process of Hacking.
Read in 8 minutesEthical-Hacking
The difference between Cyber-Security and Ethical-Hacking
In this blog, we will discuss the difference between Cyber-Security and Ethical-Hacking.
Read in 6 minutesEthical-Hacking
Overview of Ethical Hacking
Today, we will discuss Ethical Hacking.
Read in 7 minutesEthical-Hacking
How to write a Script to Perform a Vulnerability Scan of the Listed Services
Let's quickly write an automated vulnerability scan of the server using Python. This Python script will make use of Nmap
Read in 3 minutesEthical-Hacking
Blogpost
1120 posts
Discussion Threads
1572 discussions
Interview Questions
9183 questions
Cheatsheets
coming soonTechnologies
107 categories