


Penetration Testing
A penetration test, colloquially known as a pen test, pentest or ethical hacking, is an authorized simulated cyberattack on a computer system, performed to evaluate the security of the system. Not to be confused with a vulnerability assessment. The test is performed to identify both weaknesses (also referred to as vulnerabilities), including the potential for unauthorized parties to gain access to the system's features and data, as well as strengths, enabling a full risk assessment to be completed.
Trending Blogposts on Penetration Testing

How to update AjaxControlToolkit to use the latest version of JQuery?
Today we will learn how to update AjaxControlToolkit to use the latest version of JQuery by following these simple steps.
Read in 4 minutesPenetration Testing
How to increase the number of characters in ASP.Net_SessionId cookie?
In this article, we will discuss how to increase ASP.Net_SessionId cookie length by modifying cookieName attribute in web.config.
Read in 5 minutesPenetration Testing
How to increase the number of characters in ASP.Net_SessionId cookie?
In this article, we will discuss how to increase ASP.Net_SessionId cookie length by modifying cookieName attribute in web.config.
Read in 5 minutesPenetration Testing
How to install and configure Nessus with nginx in Ubuntu?
Like most scanners, Nessus is used during penetration testing and vulnerability assessments, including malicious assaults. It is a program that scans computers for security holes.
Read in 4 minutesPenetration Testing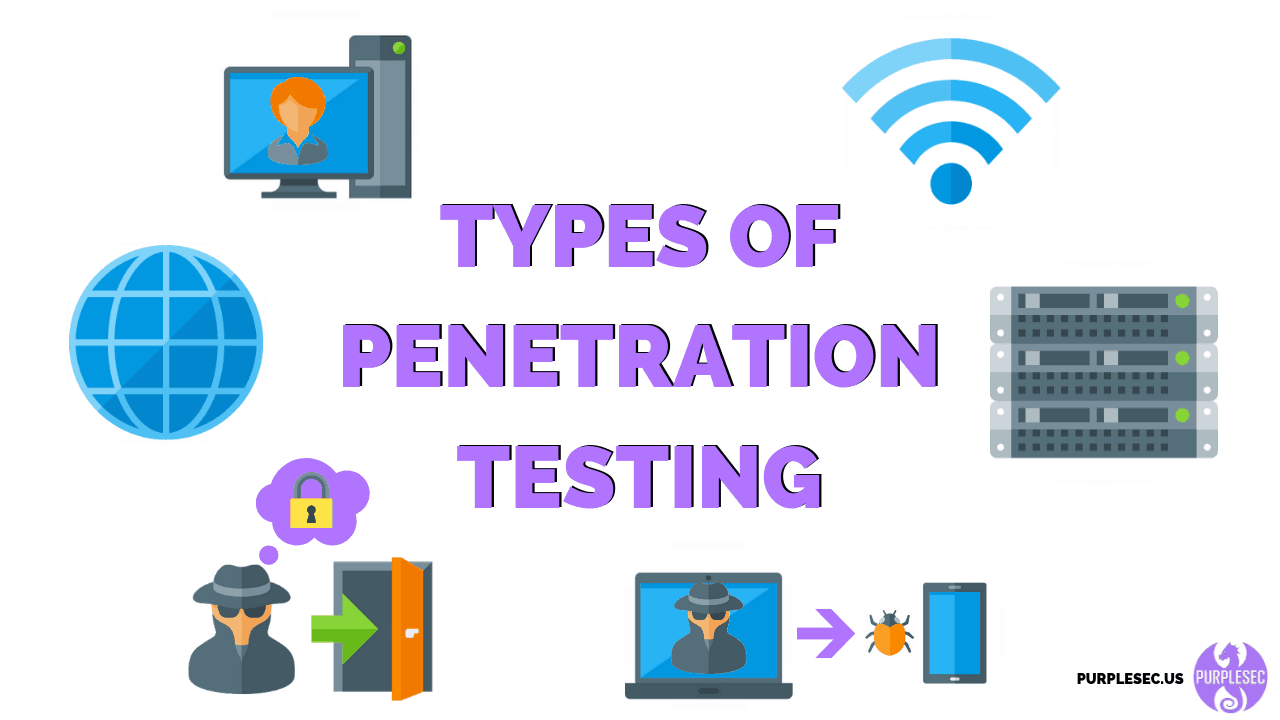
Explaining the types of Penetration testing
So let's discuss, what are types of penetration testing and their short overview.
Read in 7 minutesPenetration Testing
Top 17 Penetration Testing Tools
In this article, we will know what are the top 17 Penetration Testing tools.
Read in 20 minutesPenetration Testing
Penetration testing : overview
In this article, we will know about what is Penetration testing.
Read in 7 minutesPenetration Testing
Blogpost
1120 posts
Discussion Threads
1572 discussions
Interview Questions
9183 questions
Cheatsheets
coming soonTechnologies
107 categories
Questionaire
coming soonPopular Discussions on Penetration Testing
openI was working on atarget and i found ampcid google api key? i need to know is it dangerous to disclose it to public?
3
2
0
openHow to intercept the HTTPs traffic with BurpSuite (or any other proxy tools) for iOS mobile applications
2
1
0
openTest jquery for vulnerabilities,
2
0
0
openIs there any Penetration Testing or Security Audit guidelines (Such as OWASP) for Kubernetes?
3
1
0
openreplace/manipulate "hostname" in url without redirecting to it
4
1
0
openHow to pentest rest apis using burpsuite?
2
1
0
openVAPT Result: Link Manipulation DOM-BASED, Session token in URL in Odoo CE 10 how to resolve?
2
0
0
openUsing OWASP ZAP (and tools of the same purpose) on AWS EC2
2
1
0
openIs it enough for OWASP MASVS to display a root detection warning message, rather than terminating the app entirely?
2
0
0
openDifference between Dynamic Code Analysis and Penetration Testing?
2
1
0
opentool or framework for penetration test
2
0
0
openPenetration Testing vs Other Security Testing
2
0
0
Penetration Testing
A penetration test, colloquially known as a pen test, pentest or ethical hacking, is an authorized simulated cyberattack on a computer system, performed to evaluate the security of the system. Not to be confused with a vulnerability assessment. The test is performed to identify both weaknesses (also referred to as vulnerabilities), including the potential for unauthorized parties to gain access to the system's features and data, as well as strengths, enabling a full risk assessment to be completed.
Trending Blogposts on Penetration Testing

How to update AjaxControlToolkit to use the latest version of JQuery?
Today we will learn how to update AjaxControlToolkit to use the latest version of JQuery by following these simple steps.
Read in 4 minutesPenetration Testing
How to increase the number of characters in ASP.Net_SessionId cookie?
In this article, we will discuss how to increase ASP.Net_SessionId cookie length by modifying cookieName attribute in web.config.
Read in 5 minutesPenetration Testing
How to increase the number of characters in ASP.Net_SessionId cookie?
In this article, we will discuss how to increase ASP.Net_SessionId cookie length by modifying cookieName attribute in web.config.
Read in 5 minutesPenetration Testing
How to install and configure Nessus with nginx in Ubuntu?
Like most scanners, Nessus is used during penetration testing and vulnerability assessments, including malicious assaults. It is a program that scans computers for security holes.
Read in 4 minutesPenetration Testing
Explaining the types of Penetration testing
So let's discuss, what are types of penetration testing and their short overview.
Read in 7 minutesPenetration Testing
Top 17 Penetration Testing Tools
In this article, we will know what are the top 17 Penetration Testing tools.
Read in 20 minutesPenetration Testing
Penetration testing : overview
In this article, we will know about what is Penetration testing.
Read in 7 minutesPenetration Testing
Blogpost
1120 posts
Discussion Threads
1572 discussions
Interview Questions
9183 questions
Cheatsheets
coming soonTechnologies
107 categories